MODERN AND PROFESSIONAL
Physical Protection Module
Digitalisation and online access
Safestar enables you to keep fully electronic records of the course of service. This ensures that data on all events is secure and stored conveniently.
An important advantage is online access, so you gain fast access to the necessary data.
Your modern offer
Safestar will enable you to create a modern offer that your customers will appreciate. With us, you will turn physical protection into e-protection.
You will be able to meet increasingly higher customer expectations while maintaining reasonable prices.
Process automation
With Safestar, record keeping will be easier than ever. You will improve supervision over the work of your posts.
You will automate supervision and reporting processes, which will give you more time for other important tasks. The system will finally work for you
Training materials on the physical protection module
Control of guards’ rounds
Security logs and SafestarPatrol
Configuring reports
Four types of electronic security logs
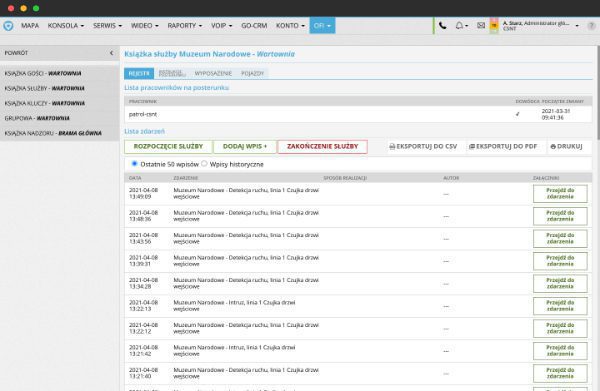
Service log
The service log is the basic type of document maintained at security posts. The service log is used to collect information about the service performed and events that occurred in the protected facility.
- beginning and end of the service
- collection of information about events
- verification of operating procedures
- registration of post equipment and employees
Entry and exit log
The entry and exit log enables you to register persons entering or leaving the protected facility. You can save the details of each person in the system and easily search for them at any time.
You do not need to register visitors once they have entered, as they remain in the system. In addition, you can register expected visitors who have given advance notice of their arrival.


Key log
The key log is a function that makes it possible to record which employees have taken or left a key and at what time. You can specify who is authorised to take a key, thus ensuring that it is not given to the wrong person.
Supervision log
The supervision log makes it possible to check security posts remotely and record the results in the system. An employee of the company’s operating centre or monitoring centre can complete further entries in local logs as a control person.

Monitoring the work of guards
Remote online supervision
Supervision automation
Safestar provides cost savings with algorithms that automate the inspection and reporting process.
The main algorithm that you can configure and use in your daily operation is virtual tours. It allows you to programme your rounds by determining at what point the next checkpoints should be recorded. In this way, the Safestar system will inform you automatically if there are any irregularities.
Lifeline
Security for guards
The most common way to supervise security guards on the premises of the protected facility is telephone calls. However, this is a cumbersome method for the monitoring centre coordinators.
Safestar has a feature called lifeline that automates this process. It allows the use of different confirmation signals.
Schedules
Lifeline makes it possible to create a schedule indicating when a security guard should check in. The system automatically checks whether the check-in signals appear at the appointed time.
Different ways of informing
The check-in signal can be a phone call, the punch-out at any checkpoint or any other signal that can be received and identified by the system.
Check out how many opportunities Safestar offers
I invite you to a call to discuss how Safestar can help your security agency grow.

