Your data is safe
Data security
Physical security
Cyber security
Backups
Internal procedures
See how we ensure security
Password strength control
The basis for secure access to any IT system is a password. To ensure peace of mind, a password should be strong enough. Ideally, it should consist of a sequence of letters, numbers and special characters. Safestar controls the strength of your password automatically.
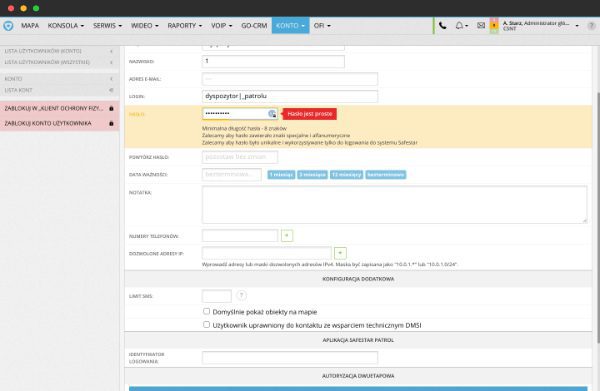
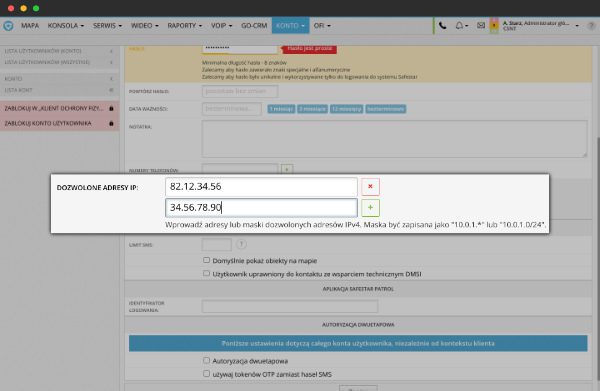
IP address filter
The IP address filtering feature allows users to log into the system only from a device that is associated with a specific IP address. Only employees who use specific equipment and specific locations can access the Safestar system.
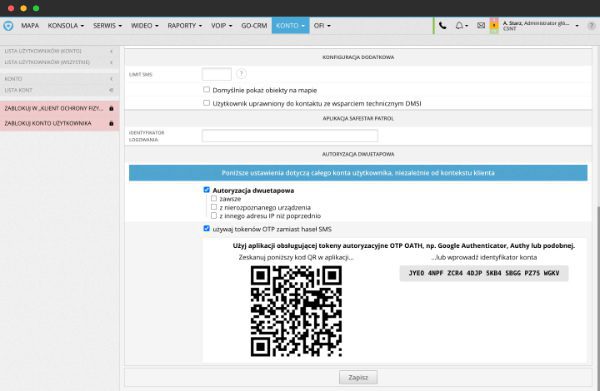
Two-step login
Two-step login provides an even higher level of security. This involves confirming the identity of the user logging into the system with another device, such as an SMS or a token.

Access levels
With Safestar, you can create different user profiles and assign appropriate rights in order for them to perform their duties. This solution makes it easier to control employee access to specific modules, groups of objects or system functionality.
GDPR in Safestar
Technical and organisational measures
To ensure the security of data transmission, we provide standard technical and organisational measures appropriate to the degree of security threat to the services provided, in particular measures to prevent unauthorised persons from obtaining and modifying personal data transmitted over the Internet.
Transmission encryption
The transmission of customer data from the system to the customer’s terminal device is encrypted using protocols that secure the transmission of data streams (Secure Socket Layer or similar).
Data encryption
The system utilises selected cryptographic security techniques for selected customer data or system access data (passwords of the Administrator and the End Users).
Backups
Backups are made to secure customer data entered into the system or other data stored in the system databases
Check out how many opportunities Safestar offers
I invite you to a call to discuss how Safestar can help your security agency grow.

